Understanding Cybersecurity Management in Decentralized Finance Series.
- ISC2 Community
- :
- Atlantic Canada Chapter
- :
- Atlantic Canada Chapter Blog
- :
- Understanding Cybersecurity Management in Decentra...
Understanding Cybersecurity Management in Decentralized Finance Series.
Understanding Cybersecurity Management in Decentralized Finance Series.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Understanding Cybersecurity Management in Decentralized Finance: Blockchain Attacks and Countermeasures - I (Article 3)
Author: Gurdip Kaur, PhD, CySA, CISSP
Blockchain is used in various sectors including healthcare, finance, government, and commerce to build blockchain-based solutions for the customers. One of the benefits of introducing blockchain in these applications is to provide security to digital transactions by leveraging cryptography, decentralization, and consensus. While the use of blockchain technology has introduced various advantages, it comes up with several cybersecurity challenges as well. Blockchain has attracted cybercriminals to exploit the vulnerabilities that exist in the technology and target organizations that use it. This article is part one of various blockchain attacks and countermeasures to prevent or avoid them.
Understanding Cybersecurity Management in Decentralized Finance is a series of articles that aims to explore a range of cybersecurity issues in decentralized finance. The articles in this series are based on the extensive research work behind our book titled ‘Understanding Cybersecurity Management in Decentralized Finance’, published by Springer in January 2023.
1. Double Spending Attack
Double spending attack is based on the fact that there is a possibility that digital money can be copied and rebroadcasted. Attackers can use the same input as an already broadcasted transaction in the network. In the first stage of the attack, the user signs off and requests for a transaction using his wallet. This unconfirmed transaction is added to the pool of similar transactions. The miner picks one transaction from the pool and applies proof of work (POW) consensus to solve complicated mathematical problems. To do so, the miner gets the verified hash of the chosen transaction and broadcasts it to the network to add a new block to the transaction. The hash contains a timestamp, information about the block, transaction data, and previous block’s hash.
In the second stage, parallel to good miner’s actions, corrupted miners also start their own chain with the verified blocks. In the third stage, the corrupted miner picks transactions and adds blocks to his isolated chain. The miner verifies the fast execution speed as compared to a real blockchain at this stage. Once done, the corrupted miner broadcasts these blocks to real blockchain. The double spending attack begins at this stage when the miner attempts to make the corrupted blockchain larger than the real blockchain. Since the block in an isolated blockchain does not have the information about the transaction (it is stored in a real blockchain), it is added by removing an existing block. This is how the corrupted miner spends his already spent money again.
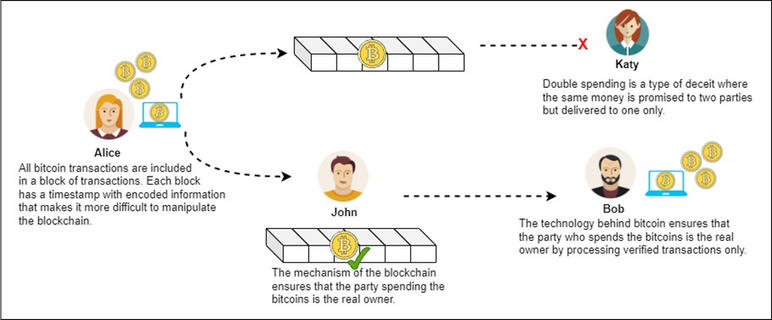
Figure 1: Overview of double spending attacks
Figure 1 provides an overview of double spending attack in which a parallel blockchain (shown in the middle of the figure) with same number of blocks is maintained. The upper blockchain represents the corrupt miner’s blockchain whereas the lower blockchain (for John) represents the genuine blockchain. However, due to the timestamp associated with each block of transaction, it becomes difficult to manipulate the blockchain. The hash values of blocks are used to verify the blocks (as shown for John’s blockchain). That is why only verified transactions (shown with a green checkmark) are processed and money is delivered to the real owner (Bob in this example).
To countermeasure this attack, it is required that an existing block is not removed to add a new block. This way the previous memory about a transaction is not removed, rather it is updated by keeping the previous information. By using this rule, whenever a new block is added to an isolated chain, the hash of that block is updated with the previous information.
2. Finney Attack
Finney attack is a type of double spending attack that can happen when a person accepts an unconfirmed transaction on the network. The attack occurs when the malicious user or miner generates a block that would include a transaction from address A to another address B, where both addresses belong to him. Both addresses produce an authentication report for the transaction which is sent by the merchant to the miner. Once this is accomplished, the miner sends payment with the same currencies, but sending from address A to address C. If the recipient accepts the transaction without confirmations from the network, the miner will release the block from his initial transaction. This invalidates the transaction with the merchant allowing the attacker to double spend. Figure 2 demonstrates the step-by-step working of the attack, considering two transactions Ta and Tb.
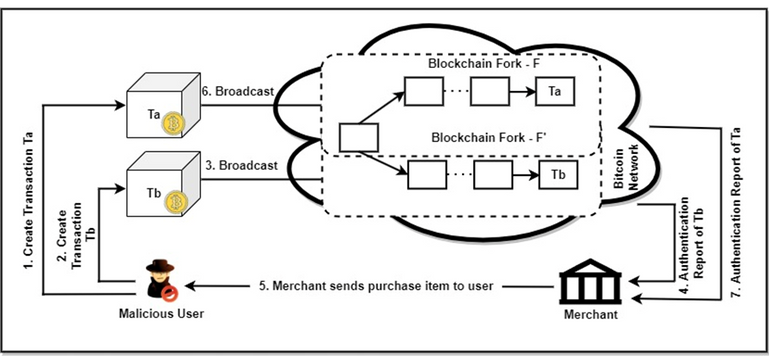
Figure 2: Finney attack
The attack can be easily demonstrated in three steps. In the first step, the attacker performs a transaction in which he sends his coins to an address owned by him. Once done, he starts mining his valid block in which the mentioned transaction is included. In the second step, the attacker manages to extract the valid block and include the transaction but does not broadcast it to the bitcoin network. Even though the transaction is not sent to the network, the attacker makes a payment with the same coins that he owns in the first transaction. Until this point the transaction is valid and the payment is genuine. In the third step, after the attacker makes the transaction and the merchant accepts it without confirmation, the attacker sends the mined block onto the network. This block is treated as a valid block, but invalidates the transaction made to the merchant.
The countermeasure to prevent the attack is to wait for a couple of transactions on the bitcoin network to consider a transaction safe and irreversible. It allows the merchant to validate a block and transaction so that it is not reversed in the middle of the processing, making a way for the attack to happen.
3. Race Attack
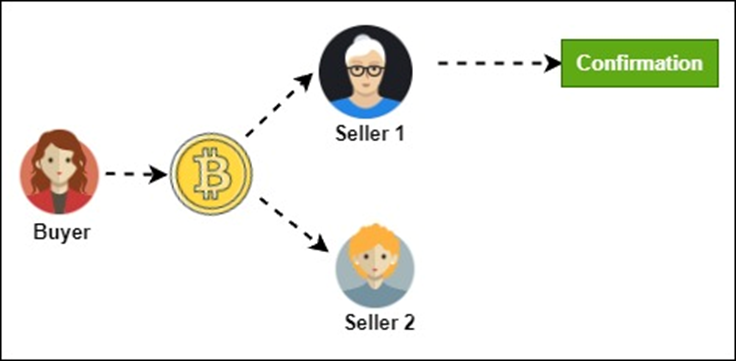
Race attack represents a race between two transactions which have been broadcast around identical time. The attack involves replacing a transaction with another one. The attack affects a vendor which accepts the payment before the transaction is confirmed, just before the transaction is reversed. This attack is performed by a malicious node that sends a payment to the recipient while a conflicting transaction to the attacker’s own account is broadcast. The second transaction is confirmed, mined, and accepted by the network in this attack. Figure 3 shows an overview of race attacks between two sellers.
Figure 3: Race attack
Race attack does not require a skilled attacker and the success rate is higher. Because of the attack, the vendor may lose a product, genuine users may be banned, and a new chain may be forked.
There are two countermeasures for this attack. The first countermeasure recommends the merchants to disable the incoming connections and select outgoing connections only. The second countermeasure emphasizes on inserting observers in the network who can communicate double spending alerts among peers as soon as possible.
4. 51% Attacks
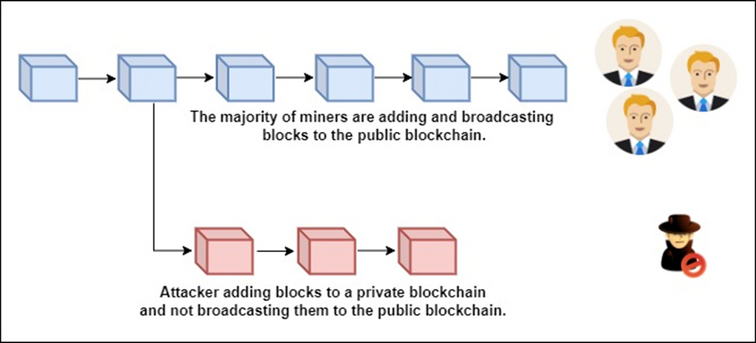
One of the most famous attacks in a blockchain is 51% attack in which a group of miners control more than 50% of the network’s mining hash rate or computing power. In this attack, the attackers prevent new transactions from getting confirmed and halt them between the merchants and clients. For the attack to be successful, attackers need to complete the proof of work faster than honest miners. As a result, their transactions will be connected to the longest chain. The more computing power the attackers own, the faster it becomes for them to make the attack happen. 51% attack can be used to reverse the transactions and spend some coins multiple times when malicious miners control more than half of the mining network. Figure 4 presents the concept behinds 51% attack.
Figure 4: Concept behind 51% attack
To prevent this attack, observers can be inserted into the network who can witness and communicate double spending taking place in the network. These activities can be reported to peers and disincentive large mining pools.
5. Brute Force Attack
Brute force or alternate history attack attempts to alter the entire history of the blockchain starting from the early blocks and including the genesis block. This is an improvement over the Finney attack. In this attack, the adversary has governance on some nodes in the bitcoin network. These nodes make a communal effort to mine blocks privately with an intention to double spend. The adversary incorporates a double spending transaction in some block, simultaneously working on the expansion of the private chain. If a merchant anticipates for ‘x’ validations before admitting a transaction and it will deliver the product after it receives ‘x’ validations. However, at a later stage, the merchant may mine the ‘x’ blocks privately and broadcast these blocks in the bitcoin network. This will result in a longer chain as compared to what was expected initially. The additional blocks will be mined by all miners in the network resulting in successful double spending.
To prevent this attack, the best practice is to insert observers in the network who can witness malicious activities happening in the network and notify the merchant about a double spending taking place in the network.
What’s next
This article introduces a few popular blockchain attacks and their countermeasures. The next article in this series will continue shedding light on some more blockchain attacks and their countermeasures.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.