Understanding Cybersecurity Management in Decentralized Finance Series.
- ISC2 Community
- :
- Atlantic Canada Chapter
- :
- Atlantic Canada Chapter Blog
- :
- Understanding Cybersecurity Management in Decentra...
Understanding Cybersecurity Management in Decentralized Finance Series.
Understanding Cybersecurity Management in Decentralized Finance Series.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Understanding Cybersecurity Management in Decentralized Finance: Blockchain Attacks and Countermeasures - II (Article 4)
Author: Gurdip Kaur, PhD, CySA, CISSP
The previous article on blockchain attacks presented double spending attack, Finney attack, race attack, 51% attack, and brute force attack. This article is part two of various blockchain attacks and countermeasures to prevent or avoid them.
1. Feather and Punitive Forking Blockchain Attack
Punitive forking is a bitcoin miner attack in which transactions from a blacklisted address are refused. The refusal happens with less than 50% of hash power. This means that when malicious miners decide to refuse the transaction, they need to convince half of the network to do so. As a result of this attack, the malicious miner creates an opportunity for other miners to earn incentives by enforcing the blacklist.
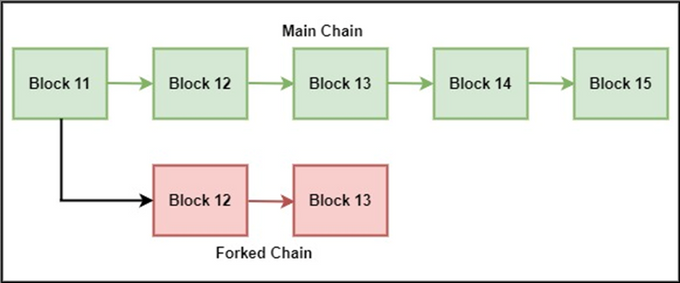
In simple words, a punitive forking attack blacklists certain bitcoin addresses owned by certain people to restrict them to use their bitcoins. The attack takes place when the attacker has most hash power. The attacker announces that (s)he will not extend the blockchain with certain blocks marked blacklisted. Feather forking is a modified version of a punitive forking attack. In a feather forking attack, this blacklisting is temporary and is suspended after some time.
Figure 1: Blacklisted blocks (marked red) due to malicious miner’s influence
Although feather and punitive forking attacks seem dangerous in the sense of blacklisting other people in the blockchain, it is not easy to carry out as the attacker does not have majority of the hash power easily. This is also a countermeasure for this attack.
2. DDoS Attack
Distributed denial of service (DDoS) attack is launched by a group of attackers to disrupt the networking tasks in the bitcoin network. It targets bitcoin currency exchanges, mining pools, eWallets, and other financial services in bitcoin. Multiple attackers launch this attack simultaneously on competing miners to take them out of the network. Figure 2 presents a general scenario in which a DDoS attack is launched. As evident, the hacker uses several compromised machines called bots to create a botnet that targets the blockchain as per instructions received from the hacker.
Figure 2: DDoS attack
The intention of the attack is to increase the incentives and computing power of the attackers. In this attack, the adversary exhausts the network resources to disrupt legitimate services accessed by the genuine users. To instantiate, an honest miner is congested with requests from many client transactions launched by the adversary. After a while, the miner will start discarding all the incoming requests from genuine users.
The main method to mitigate DDoS attacks is to continuously monitor the bitcoin network traffic coming from Tor or any other user-defined web service. Machine learning techniques can also be used to help classify malicious traffic. Moreover, the network should be configured in such a way that malicious packets and requests from additional ports are restricted or blocked. A third-party DoS protection scheme can also be implemented.
3. Liveness Denial Attack
Liveness denial is a type of DDoS attack in proof of stake (PoS) protocols. In this attack, some or all the validators decide to act and block transactions by stopping publishing blocks. Since validators stop publishing, the blockchain comes to a halt as no more blocks are validated. Even if the validators are united to stop publishing new blocks, the bitcoin network is not compromised by them. In cases where liveness cannot be validated, the community decides to fork blockchain and remove inactive validators. Certainly, the validators who perform this attack jeopardize their position and stake in the network.
The most debatable countermeasures to liveness denial are the same as that used for DDoS attacks. This includes prominent blockchain technology features such as decentralization and consensus mechanisms.
4. Tampering or Delay Attack
Tampering or delay attack is related to the scalability measures of the bitcoin network. In this attack, an adversary can exploit the scalability measures to delay the delivery of advertisement messages. The adversary acts as a full bitcoin node in this attack where he has access to the entire blockchain. The objective of the adversary is to temporarily deny the delivery of an object from a specific node. The adversary can capitalize on this short span of time attack to turn it into a prolonged attack, preventing the delivery of the message.
There are two requirements for the attack to succeed. First and foremost, the adversary must be the first peer to send a message advertisement of an object to the target node. If the target node requests an object from a node that is not under the control of the adversary, then he can do a little to prevent that node from sending the object to the target node. However, if an adversary can first advertise an object via a message to the target node, then the node will abstain from requesting the object from another node. To do so, the adversary needs to be the first peer of the target node. Second, the target node should wait for an ample amount of time before requesting an object from another peer. The longer the target node waits for the adversary to send a message, the devastating impact of the attack would have on the target node. The attack can be extended to delaying blocks and transactions.
There are several countermeasures to prevent delayed attacks. The first one is to use dynamic timeouts. The blockchain uses static timeout to tolerate network delays, assuming that all nodes and resources in the bitcoin network are homogeneous. However, this is not the case. The second countermeasure is to update block advertisements before transmitting blocks. Like transaction advertisements, bitcoin nodes must keep track of the block advertisements.
5. Quantum Attack
Quantum computing or quantum computers, as one can refer to them, will be the most powerful computers in the future that can break almost all encryptions used today to secure the bitcoin network. According to an estimate, approximately one quarter of the bitcoins in circulation today are vulnerable to quantum attacks. Most of the encryption relies on the use of public-private key pairs to encrypt sensitive data. Cryptography is used to create a hash of the sensitive data so that it can be protected from adversaries.
Quantum computers are supercomputing machines that can perform computations in an unprecedented manner. Some quantum attacks are targeted at stored data while others aim at the data in transit. Blockchain presents a unique challenge for quantum-safe cryptography due to its decentralized nature and governance structure. Cryptocurrencies are highly prone to quantum attacks in the future. The major advantage that quantum computing offers is the speed of computations in performing hash of a proof of work (PoW) used by bitcoins. A quantum computer can perform the same computations as done by a classical computer in one-fourth of the time.
Quantum computing is assumed to undergo future improvements to improve the speed of computations to increase to 100 times of what they have today. This generates an alarm for the cybersecurity professionals to protect the bitcoin networks which are dependent on cryptography.
What’s next
This article is part two of popular blockchain attacks and their countermeasures. The last article in this series will present challenges and issues with decentralized finance.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.