Understanding Cybersecurity Management in Decentralized Finance Series.
- ISC2 Community
- :
- Atlantic Canada Chapter
- :
- Atlantic Canada Chapter Blog
- :
- Understanding Cybersecurity Management in Decentra...
Understanding Cybersecurity Management in Decentralized Finance Series.
Understanding Cybersecurity Management in Decentralized Finance Series.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Understanding Cybersecurity Management in Decentralized Finance: DeFi Platforms and Related Cybersecurity Issues (Article 2)
Author: Gurdip Kaur, PhD, CySA, CISSP
Decentralized finance platforms allow users to lend or borrow funds from others, speculate on price changes using derivatives, trade cryptocurrencies, insure against risks, earn interests on crypto saving accounts, and play online games. DeFi does not rely on any intermediary parties such as banks, exchanges, or brokerages. It offers customers all these benefits by using smart contracts on blockchain.
Decentralized finance finds wider applications through innovations such as decentralized exchange, P2P lending, crypto loans etc. Majority of these applications are available on different DeFi platforms. DeFi apps are powered by smart contracts and can strip traditional intermediaries like banks. This article puts forward popular DeFi platforms and investigates the security issues of those platforms.
DeFi Platforms
This section presents a non-exhaustive list of popular DeFi platforms. For understanding some terms, please refer to Definitions at the end of the article.
1. Ethereum
Ethereum is a secure decentralized and generalized transaction ledger. It offers a value transfer system that can be shared across the world and is free to use. It aims to provide an end-to-end integrated system for building software. The main objective of the Ethereum project is to facilitate transactions between consenting parties who otherwise have no means to trust each other.
Ethereum is an open-source blockchain technology with smart contract functionality. It uses Turing-complete programming language to write smart contracts and decentralized applications which can create their own set of rules for ownership. Ethereum consists of two types of accounts: externally owned accounts and contract accounts. Externally owned accounts are controlled by private keys. These accounts do not have any code, so they use the private key to sign the transaction. Contract accounts are controlled by their contract code. Every time a message is received, corresponding code is activated to read and write it to internal storage and write messages in response. In nutshell, Ethereum first loads the program in memory, executes it, and finally stores the results in blockchain.
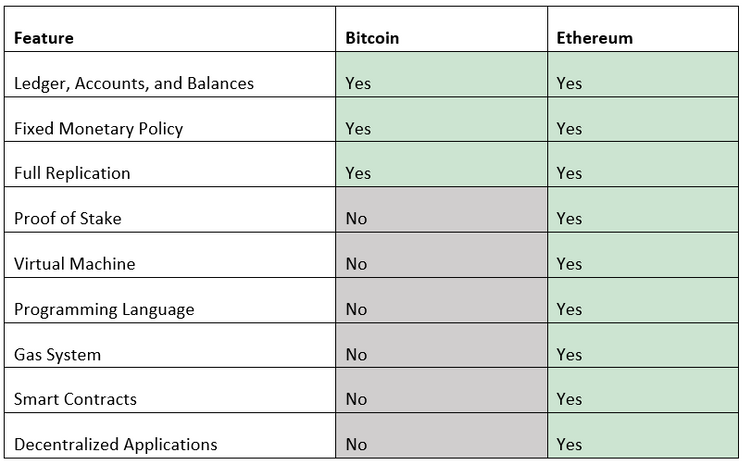
For clarity, Ethereum is different from bitcoins. Ethereum has its own currency called Ether and is abbreviated as ETH. Although some features are common in both, yet there are some features which clearly distinguish the two. The following table distinguishes Ethereum from bitcoins for a better picture.
The following table distinguishes Ethereum from bitcoins for a better picture.
Table 1: Differences between bitcoin and Ethereum
Ethereum implements the blockchain paradigm which is cryptographically secure and possesses a single instance of a machine which is shared with everyone. Ethereum consists of three main components: transaction, state, and block. A state machine refers to something that reads an input and transitions to a new state. The state of transactions is grouped together into blocks. The blockchain blocks are bound together with cryptographic hashes. A block contains a header and a body. Header holds the metadata about the block. It also stores the hash of the previous block. The purpose of every block is to execute transactions.
2. Binance Smart Chain
Binance Smart Chain (BSC) is best described as a blockchain that runs in parallel to the Binance Chain. It provides two-fold functionality by retaining the high performance of the native blockchain and supporting the smart contracts. The Binance Smart Chain offers several advantages as it brings the best of two technologies together. It reduces time and cost to transfer assets in a short span of time. It also allows developers to leverage cross-chain communication and Ethereum compatibility. BSC is a sovereign blockchain which provides safety and security to all users and developers.
The focus of Binance Chain is on its decentralized application called “Binance DEX”. The application has shown its low latency matching with large capacity headroom by handling voluminous transactions in a short span of time. BSC’s most extendable feature is smart contracts and virtual machine function. Despite the high demand of adding smart contracts to BSC, it is a hard decision to make. The reason behind this is the slowdown of BSC after adding smart contracts. However, it can be achieved by adding a parallel blockchain to the current BSC that will retain the high performance and support smart contracts at the same time.
The principle of adding a parallel blockchain will provide many benefits including Ethereum compatibility, consensus, and governance. It will also retain the features of the current Binance Chain. Parallel blockchain reduces the time required for execution of transactions.
3. Avalanche
Avalanche is a high-performance, scalable, customizable, and secure blockchain platform. It targets highly scalable and distributed applications. It builds application-specific blockchains comprising both permissioned (private) and permissionless (public) deployments. Avalanche aims to build, transfer, and trade arbitrarily complex digital assets.
Figure 1: Working of Avalanche consensus protocol
Protocols in the Avalanche family operate through repeated sub-sampled voting as presented in Figure 1. When a new transaction is issued, it is confirmed whether it is valid or not. This confirmation is provided by the validator. If the transaction is invalid, it is ignored. On the contrary, if the transaction is confirmed to be valid, it is added to the list of valid transactions. Then the process of repeated random sub-sampling starts in which K random validators are selected and their confidence is measured in terms of their weighted stake.
If the measured confidence meets a threshold value, the transaction is accepted, otherwise the confidence value is updated. The last step in this procedure is to reject all transactions that conflict with the accepted transaction.
4. Polygon
Polygon is best described as a protocol and a framework for building and connecting Ethereum-compatible blockchain networks. Polygon combines the best of Ethereum and sovereign blockchains into an attractive feature set, including scalability, flexibility, and sovereignty from stand-alone blockchains and security, interoperability, and developer experience from Ethereum. Alternatively, Polygon leverages security as a service by combining these networks.
Polygon’s architecture consists of four layers: Ethereum layer, security layer, Polygon network layer, and execution layer.
- Polygon chains can use Ethereum, the most programmable blockchain in the world.
- The security layer is a specialized, non-mandatory layer providing a set of validators to periodically check the validity of Polygon blockchains.
- The Polygon network layers provide consensus, transaction collation, and block production.
- Finally, the execution layer is responsible for interpreting and executing transactions included in the Polygon network.
Security Issues of DeFi Platforms
DeFi platforms offer high leverage, liquidity, and interconnectedness among users. However, these features come with severe vulnerabilities that are discussed in this section.
1. Centralization: DeFi purports to be decentralized, but complete decentralization is illusory. A key issue in full decentralization is that smart contracts are unable to provide a full range of opportunities that leverage interactions with users. All DeFi platforms have central governance frameworks outlining how to set strategic and operational priorities. Therefore, all DeFi platforms support centralization to some extent.
2. Fragility: Crypto assets are fragile and are designed to target a fixed face value. This arrangement results in mismatches between risk profiles and stablecoin liabilities. Liquidity mismatches and exposure to market risk increases the possibility of investor runs.
3. Software Bugs: DeFi applications make use of smart contracts which are programs developed in a programming language. Software is exposed to several bugs which can be exploited by malicious actors. This is called smart contract risk. Further, smart contracts are open-source which means there may be involvement of naive developers who might not have followed the programming standards, leading to software flaws.
4. Scams and Cyber-attacks: DeFi platforms are vulnerable to scams and cyber-attacks. One of the most important scams is rug pull scam. It is a type of exit scam in which malicious actors create a new token, launch a new liquidity pool for it, and pair it with a base token. A liquidity pool is a large pool of tokens used for trading. To execute the scam, scammers keep a significant portion of total supply to themselves once the token launches. Once investors start adding liquidity to the pool to earn and the pool reaches a threshold, scammers dump all their tokens to the pool. It drops the price of newly created tokens to nearly zero, leaving investors empty handed.
5. Phishing: DeFi platforms are susceptible to phishing attacks. In this type of attack, scammers pretend to be an official company to trick victims into revealing sensitive information. Phishing attacks are very common in crypto. A swarm of bots is used to launch the attack using social media. The attack looks so genuine that even a Google form is created, and victims are asked to fill in their information such as their wallet.
Definitions
- Turing Completeness: Ethereum can compute any program that a Turing complete machine can. However, Ethereum is powered by blockchain.
- Consensus Rules: The set of rules used to validate a transaction and a block.
- Proof of Work: A decentralized consensus mechanism that requires members to expend effort in solving an encrypted hexadecimal number.
- Gas System: A system that measures the computational effort required to execute specific operations on an Ethereum network.
- Stablecoin: It serves as a means of payment and store of value for a range of DeFi transactions.
What’s next
This article introduces popular DeFi platforms and cybersecurity issues associated with them. The next article in this series will shed light on important blockchain attacks and their countermeasures.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.