- ISC2 Community
- :
- Discussions
- :
- Threats
- :
- The Code is a Changin'
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The Code is a Changin'
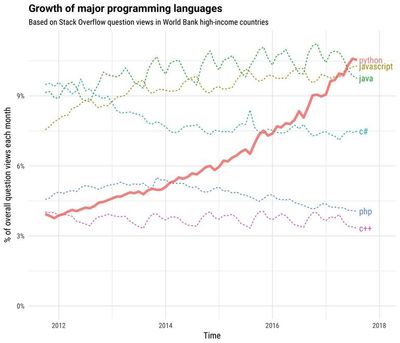
The vast majority of serious malware over the past 30 years has been written in Assembly and compiled languages such as C and C++ (sorry Cobol lovers you didn't make the list). Over the last decade we have seen the emergence of malware written in interpreted languages. Case in point: Python. Developing Python malware takes advantage of a massive ecosystem of open-source packages and repositories. Almost anything you could think of, someone has already built it using Python. This is a huge advantage to malware authors as simplistic capabilities can be picked à la carte from GitHub or other repo's. On top of that the portability of malicious Python code is exacerbated by the fact that you don't need an interpreter, native executable can be built on the fly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I would really have to disagree with these findings. Malware in general is trying to hit the most people as possible and the average person does not have a python interpreter installed. It seems like they could only target advanced users and developers which in most cases should have enough experience to see most malware coming...
Just my .02
John-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
One way of doing it is to bundle the Python interpreter, but you can just image how large a file that would be. Another simpler way is to just convert Python code and create Windows and/or Linux executable.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You can convert Python code into an executable?!? I did not know that. Learn something new every day!
John-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You could if Pyinstaller or similar is on the machine but this quickly devolves into a "chicken before the egg" scenario. In order to create the executable you need control over the target first which negates the need to create the executable on the target.
I think what you are eluding to is to create the executable before sending it to the target otherwise your indicating taking over an already compromised target or intellectual sleight of hand.
- b/eads
