- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- NMAP and OT Scanning
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
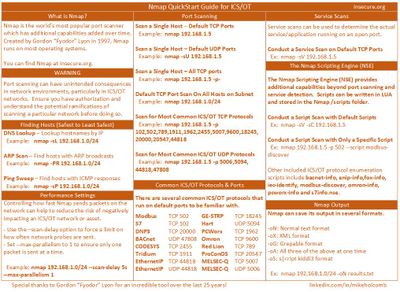
NMAP and OT Scanning
A colleague posted this on another feed.
This is excellent information for anyone considering using NMAP to scan their OT/ICS environment.
He also provides great advice as follows:
Before you just starting scanning away in your OT environment though, consider the following:
1. Any active scanning tool, such as Nmap, has the potential to impact system responsiveness and availability. Many OT assets, especially older ones, can have interoperability issues when scanned by Nmap resulting in the asset failing, reloading or even completely crashing and needing to be replaced.
2. If risk to physical safety, environmental safety or production are ever at question for your environment, do not use Nmap in your OT network.
3. Active scanning should never be used inside production facility networks against Level 0 to 2 assets.
4. Consider using Nmap for scanning of "traditional IT systems" that are in use within the OT network such as data historians, engineering workstations and domain controllers running Windows or Linux. Such testing should be coordinated in testing windows. Conducting Nmap on a regular basis against these very popular targets for attackers could help discover if a malicious service has been installed on these assets without your knowledge. Only scan these resources when a secondary system can be made immediately available to eliminate any risk to impacting production.
5. Reserve Nmap scanning for all other OT assets for any backup facilities or testing during Factory Acceptance Testing (FAT)/Site Acceptance Testing (SAT).
6. Be sure to scan your external Internet-facing ranges to ensure you do not have any assets directly exposed to the Internet.
Bottom line: BE CAREFUL
d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@dcontestiMost critical infrastructure engineers, would not permit such tools to be let loose within their environments, especially if you look like a consultant and not in an engineering overall and work safety boots.
Plus the other major thing, which has been left out is actually obtaining formal written approval from your organisation to actually conduct passive scanning rather than active scanning within an OT environment.
Conducting such an exercise without formal permission, could lead to termination or even prosecution under the various Crimes Act or Computer security legislation within that particular country.
Normally, even trained and certified security testing practitioners would be actively supervised / monitored to ensure that no disruption, or damage is caused to even critical infrastructure. It has been known for one of the big four consultancy companies to perhaps go a little Gungho and cause major damage to normal organisations let alone OT environments.
Where you state be careful, perhaps that should be amended, to do nothing without formal written approval from the organisation or OT engineers.
Regards
Caute_Cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So this is where we disagree. I work in an ICS environment and have done so for awhile.
Many folks many not want to run these tools in their environs but many us find ourselves in positions that we need to understand the entire picture, thus we will rely on tools such as NMAP.
Although I do agree that not everyone should be running these tools, they can be run safely and this was intended to provide some insight.
I have seen systems crashed for even using "finger" on them, so anything that is used in ICS should be used with great caution.
Would I ever let a consultant run these tools? That is a different question and might also depend on whether I wish to keep my job or not. If the Senior (and I do mean senior management) get convinced that these tools should be run, sometimes, one must bend to their wishes. In my case, I had specifically trained staff that would "Oversee" the consultants and not let them just hit enter. Also not let them touch certain systems.
As in any environment, one must be careful especially when dealing with some of the Level 1 and Level 2. systems. In my case, it really was not the fear of losing data but the fear of losing a life (remember I worked in Heavy manufacturing).
d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@dcontesti Having witnessed someone actually being accused and subsequently terminated by running an unauthorised vulnerability tool, in a country where under the Crimes Act, it is a criminal offense.
Unfortunately for expediency the person did not obtain formal approval to run the tool.
I would agree with you in normal organisations without critical infrastructure.
In terms of consultants who are brought in as an independent auditors, we had no choice - the consultant went amok, as he connected himself to a high speed switch, and had not realised the ramifications of his choice in a complex multi-tiered government architecture. He shall we say felt liberated and not constrained. Yes, they had authority, but was asked to stop, when certain systems could not handle the barrage of requests internally.
A formal complaint was made.
Yes, I do understand the issues with IC environments, but normally the appropriate tools are applied after great scrutiny from the chief engineer after having been thoroughly tested too by the other engineers too.
From my experience, and living in a country whereby vulnerability tools are deemed to be a weapon in the eyes of the law, one has to be very careful in all circumstances wherever they are applied.
Regards
Caute_Cautim