- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- Re: HSM in the cloud for Cryptographic Key Managem...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
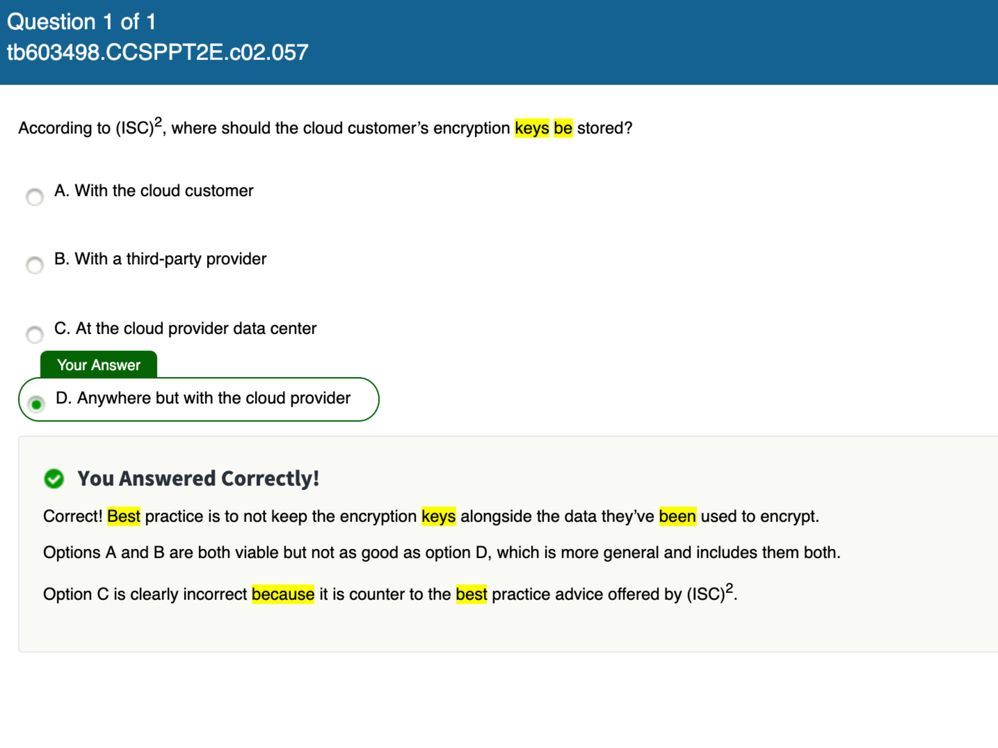
HSM in the cloud for Cryptographic Key Management
I have a project that requires cryptographic key management utilising FIP140-2 level 3. I was considering using AWS- Cloud HSM, but when studying for my CCSP I can across the attached question which reminded me that encryption keys should NOT be stored with the cloud provider, Do this mean I can have the keys stored in the same region, with the same provider but just in a different AWS account? AWS Cloud HSM claim to have FIP140-2 level 3 and once this service is taken by the customer a dedicated, they are guaranteed a dedicate piece of hardware, i.e. not part a a shared tenancy infrastructure.
I could consider using a purely software based HSM at FIP140-2 (level 2) such as Hashicorp vault; if I do this does it need to be with an entirely separate environment, so I could use the keys from Google or Microsoft or on-prem if another Cloud provider is consider to be the same type of environment - which wouldn't be allowed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Kind of a standard response for you here, but what are the benefits, costs and risks involved with any solution?
Once you know those, it's simply a matter of do the benefits and costs stack up when compared to the risks, and, ultimately, is the level of risk low enough for your organisation to be able to accept?
If the level of risk is deemed too high, can you employ any mitigations to lower the risk to an acceptable level?
If you can't, you need to investigate another solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@AlecTrevelyan Often the costs stack up against you, and the risks are more acceptable. A lot of Cloud Providers provide this facility. The costs of HSMs over a five year hardware period is high, so there has been a general shift to offering HSMs in the Cloud as a service for a few years now.
However, I see quite a few organisations, actually use the HSMs in the Cloud as a service, but they bring their own keys or BYOK as a mitigation. So effectively there are still in charge of their own destinies.
There is a general exodus especially during these times of Pandemic to shift to digital transformation and instead of heading for the hills or Doomsday Preppers they head for the Clouds instead.
Regards
Caute_cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@Caute_cautim - you're preaching to the converted!
The question in the original post is based around the use of cloud hosted HSMs:
Can they use AWS CloudHSM in a different AWS account to the Production systems and still provide enough separation vs using another provider's cloud HSM?
My answer was to use a standard risk management based approach to assessing the suitability of any solution.
BYOK is a great option to give you back that local control, but is effectively the same as using another provider's HSM (be that cloud or on-prem) for key creation and storage.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@AlecTrevelyan I agree, look under the hood. I would also add I am seeing a great deal of people accepting Opensource software within services offered across many cloud providers. I wonder how many people actually carry out Security & Privacy by Design testing, rather than reach out to NIST, DISG, CIS and others to check whether they can be hardened or even look up whether exploits exist rather than merely accepting it?
Are we letting down the guard in desperation in terms of getting on the cloud or just becoming lazy and reluctant to test or asking the appropriate questions?
Especially as a great deal of these cloud based services are based on GitHub, and we all know who owns GitHub these days - whose section was actually recently compromised.
Regards
Caute_cautim