- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- A brief summary of my studying the Orange Book
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
A brief summary of my studying the Orange Book
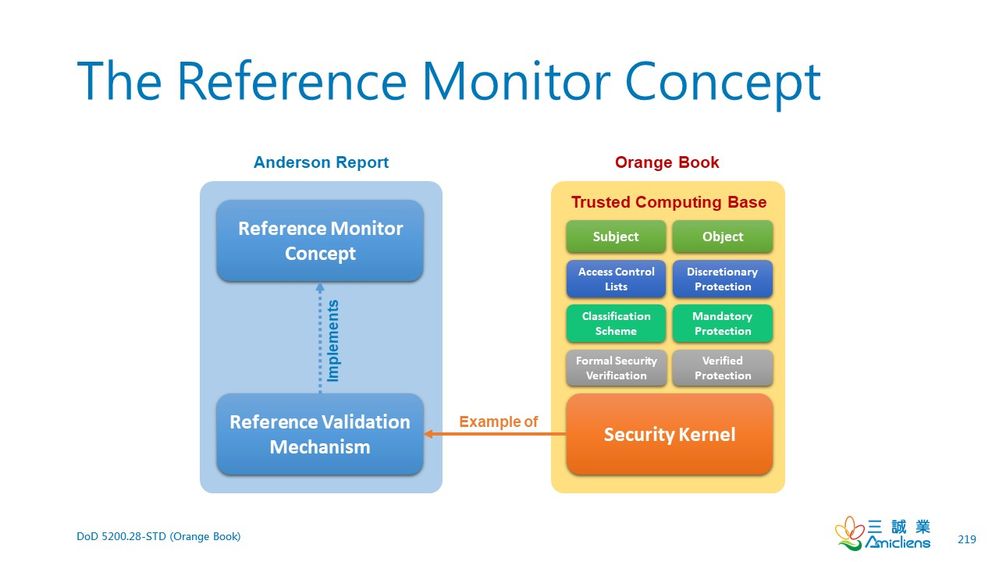
When studying Domain 3, Security Architecture and Engineering, of the CISSP CBK, it is not uncommon that CISSP aspirants are confused by the concept of the reference monitor. The following is a summary of my studying the Orange Book to clarify it.
https://wentzwu.com/2019/04/17/the-reference-monitor-concept
Best regards,
Wentz Wu, CISSP-ISSMP,ISSEP,ISSAP/CCSP/CSSLP
https://WentzWu.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@wentzwu wrote:When studying Domain 3, Security Architecture and Engineering, of the CISSP CBK, it is not uncommon that CISSP aspirants are confused by the concept of the reference monitor. The following is a summary of my studying the Orange Book to clarify it.
https://wentzwu.com/2019/04/17/the-reference-monitor-concept
Wentz,
Thank you. Your illustrations here lead to a nice comparison. However, for most of the younger members of our community, I'd like to point out that the Orange Book is the nickname for an out-of-date computer security publication from the U.S. National Security Agency (NSA), officially titled
DoD 5200.28-STD "Orange Book", DoD Trusted Computer System Evaluation Criteria (December 26, 1985).
It is the most prominent and well-known book in a series of computer security publications from NSA, called the Rainbow Series, since each volume was printed with a different distinctive color cover. They were written and maintained in the 1980's and '90's.
None of the Rainbow Series publications are current or currently valid, but they are an important set with historical significance. They are no longer maintained or published by NSA or the Department of Defense (DoD). However, the U.S. National Institute of Science & Technology Computer Resource Center (NIST CRC) makes many of them available for historical purposes. See
White Paper: DoD Rainbow Series
and further links back to the more complete collection at the
Federation of American Scientists
As noted by the FAS, some of the Rainbow Series books were superseded by the
Common Criteria Evaluation and Validation Scheme (CCEVS)
as maintained by the National Information Assurance Partnership (NIAP).
Finally, some U.S. national security organizations and some contractors to those organizations prohibit use of government or corporate computers and networks to access the FAS.org web site. Community members at U.S. DoD, DHS, and Intel Community organizations, and at companies with contracts with those organizations should consult with their information security offices before connecting to FAS.org.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, Dr. Shelton, for your informative supplement.
Best regards,
Wentz Wu, CISSP-ISSMP,ISSEP,ISSAP/CCSP/CSSLP
https://WentzWu.com
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Although times and reference sources and materials have changed "security kernels" are still one of the most important security engineering topics to grasp for a CISSP. Searching through Common Criteria evaluations will give you good practical knowledge on product conformance claims. Testing of secure designs goes from mathematical formalism to validating that those principles are verified in OS designs. It is the most fun reading you can have!