What is the difference between Data Dispersion (using erasure coding on CBK pg 92) and Bit Splitting (CBK Pg 106) and how does Raid 5 "make sure that a single CSP does not have access to the entire data set"?
Could anyone also please clarify the following statements on Pg 98 of the CBK:
"Volume storage encryption requires that the encrypted data reside on volume storage. This is typically done through an encrypted container, which is mapped as a folder or volume.
Instance-based encryption allows access to data only through the volume OS and
therefore provides protection against the following:"
Is the encryption of the data stored in the volume done in the Container (ex: Docker?) that is running on the (VM?) Instance that is processing this data?
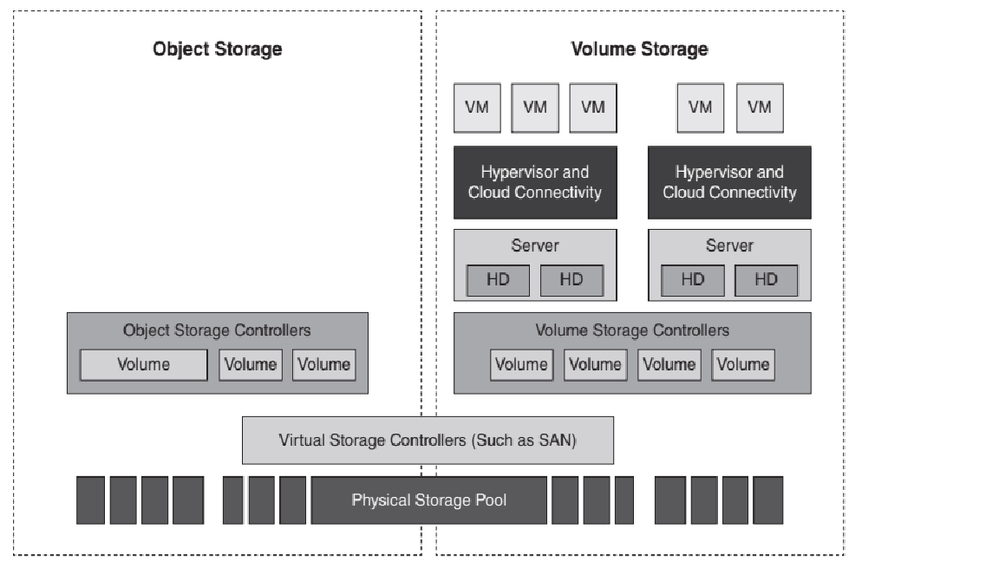
Where is the "Volume Storage Encryption" occurring in the following picture (from pg 88 fig 2.7)?