- ISC2 Community
- :
- Certification
- :
- Exam Preparation
- :
- Re: Checking some answers to a practice test
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Checking some answers to a practice test
I just took a practice test and I don't understand some of the answers they say are correct. Can anyone explain them? Or are the questions broken?
17. Cloud computing is based on which approach to service delivery: the answer was "Virtualization or thin client technology." My answer "virtualization" was wrong. I wasn't aware the thin client technology was part of it. Not mentioned in anything I read (that I remember) or in the class.
32. Information Rights management (IRM) is generally associated with the following attributes: (notice it said "attributes.")
Right answer: Data rights management, the use of role-based access control, the installation of a local client agent, and the ability to integrate with the data loss prevention (DLP) solutions
My selected answer was: Role-based access control, the installation of a local client agent, and the ability to integrate with the data loss prevention (DLP) solutions
It had everything that the "right" answer had except "data rights management." Is drm an attribute or a technology? And besides, isn't IRM the same term as DRM?
65. A risk assessment is based on the following, in order:
The right answer is: Threat, vulnerability, probability, impact and risk determination.
My answer was: Vulnerability, threat, impact, probability and risk determination.
My class notes and the photo of the instructor's drawing clearly says:
Identify assets
Identify vulnerabilities
Identify threats
Identify exposure factor (impact)
Identify Likelihood (probability)
Perform qualitative risk analysis
perform quantitative risk analysis. which means that my selected answer was correct. Thoughts?
135: Generally, there are two types of cooling, and the return air temperature is based on:
The right answer: Latent cooling (remove moisture) and sensible cooling (remove heat),and the temperature is measured at the inlet point.
Well that's just wrong. The air temperature is measured as it exits the room, not as it enters the room. My selected answer was: Latent cooling (remove moisture) and sensible cooling (remove heat),and the temperature is measured at the exhaust point.
Thoughts?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So this is hard to answer.
First whose practice test is it? Is it on the internet, from the course provider?
Second what were all the answers? to the questions.
Whose training did you take.......what references did they provide?
Sorry for so many questions, but I cannot answer your questions without some information.
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks, I got the practice test from Training Camp. Training camp was offered to me by my employer, so I didn't inquire about their references. (or did you mean what materials did they reference?) The material we used was the official ISC2 publication "Certified Cloud Security Professional Official (ISC)2 Student Guide." IMHO, this guide is very poorly written. But that's the subject for another thread.
17. Cloud computing is based on which approach to service delivery:
a) virtualization
b) thin client technology
c) Virtualization or thin client technology
d) Tightly coupled architectural models
I answered "a," but the correct answer was "c." Really?Just the fact that they have "or" in the answer made it not seem correct. That combined with not having heard about thin clients since the early days of the internet made that answer seem wrong.
32. Information Rights management (IRM) is generally associated with the following attributes:
a) Data rights management, the use of role-based access control, the installation of a local client agent, and the ability to integrate with the data loss prevention (DLP) solutions.
b) Data rights management, the use of rule based access control, the installation of a local client agent, and the ability to integrate with data loss prevention (DLP) solutions
c) role-based access control, the installation of a local client agent, and problems with interoperability with solutions such as data loss prevention (DLP) solutions.
d) Role-based access control, the installation of a local client agent, and the ability to integrate with data loss prevention (DLP) solutions.
I answered "d" because they said they were looking for attributes. The only difference between "d" and the right answer "a" is it mentions data rights management, which is a technology not an attribute.
65. A risk assessment is based on the following, in order:
a) vulnerability, threat, probability, impact, existing controls, and risk determination.
b) vulnerability, threat, impact, probability, and risk de3termination
c) threat, vulnerability, existing controls, probability, impact and risk determination
d) threat, vulnerability, probability, impact, and risk determination
I answer b, which matches my instructor's drawing in class. The correct answer is D.
My class notes and the photo of the instructor's drawing clearly says:
Identify assets
Identify vulnerabilities
Identify threats
Identify exposure factor (impact)
Identify Likelihood (probability)
Perform qualitative risk analysis
perform quantitative risk analysis. which means that my selected answer was correct.
HOWEVER ... between when I wrote that and now, I found this in the Student Guide:
Risk Management Process
An organization will conduct a risk assessment (the term risk analysis is sometimes intercahgned with risk assessment) to evaluate:
- threats to its assets
- vulnerabilities present in the envrionmnet
- the likelihood that a threat will be realized ...
- the impact that the exposure being realized will have on the organization
- Countermeasures available ...
- the residual risk
So that matches the right answer, D. So I guess that one is now answered. Go with the official ISC2 guidebook.
135: Generally, there are two types of cooling, and the return air temperature is based on:
a) latent cooling (remove moisture) and sensible cooling (remove heat), and the temperature is measured at the inlet point.
b) latent cooling (remove moisture) and sensible cooling (remove heat), and the temperature is measured at the server exhaust point
c) latent cooling (remove heat), and sensible cooling (remove moisture), and the temperature is measured at the inlet point.
d) latent cooling (remove heat) and sensible cooling (remove moisture), and the temperature is measured at the server exhaust point.
Well that's just wrong. The air temperature is measured as it exits the room, not as it enters the room. My selected answer was: Latent cooling (remove moisture) and sensible cooling (remove heat),and the temperature is measured at the exhaust point.
Thoughts?
Thank you very much for your help!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
And here is another one that I don't understand:
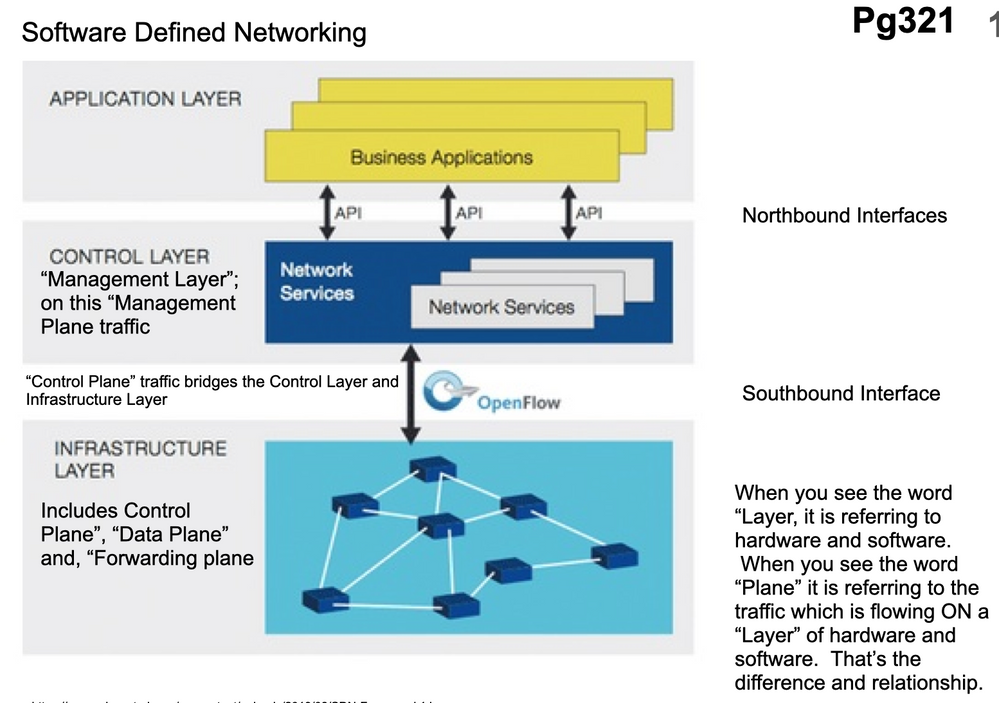
Cloud environment can be separated into three layers, which are referred to as the:
a) compute layer, the management plane, and the infrastructure layer
b) application layer, the management plane, and the infrastructure layer
c) application layer, the control plane, and the infrastructure layer
d) service layer, the platform layer, and the infrastructure layer.
My answer was d, the right answer was a.
Now this confuses the heck out of me because of a few things. First, a layer is an architectural component and a plane is traffic. (or so I've been told). So the only suitable answer was d. But even if you let that go ... second, they mix up plane and layer in answers a, b, and c. That seems inconsistent. Third, what i'd personally say was the right answer would be
Application (or compute) layer | Control Layer | Infrastructure Layer
The management plane runs on the control layer, sometimes also called the management layer. The control plane runs on the infrastructure layer and makes the connection to the control layer. The data plane (also called the forwarding plane, also called the data forwarding plane) runs on the infrastructure layer.
So by what I know, none of the answers is correct. But even if you try to figure out which one is least wrong, and you accept that management plane is the central layer (since it does run there after all), then a and b are identical because application layer and compute layer are the same. And, given that my class drawing says "application layer," i would have chosen b. Which is wrong. Anyway, here's a screen shot of the information I've been referencing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Always remember this,
- Cloud Applications (SAAS)
- Cloud Software Environment (PAAS)
- Cloud Software Infrastructure
— Computation Resources (IAAS)
— Storage (DAAS)
— Communications (CAAS)
- Then comes Software Kernel which sits on
- Firmware /Hardware
Now, looking at above, just try answering
1.the definition of Platform?
2. Is Infrastructure part of Platform? If not then why ?
3. Now relate this >> Computational Resources ( Processing, Memory ,etc ) sits on Infrastructure components and it’s controlled by administration or management
Their answer is right definitely because a Platform is whole set of everything including Infrastructure and compute layers while management is being referred as a plane.
Hope this clarifies
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@altoflyer wrote:Thanks, I got the practice test from Training Camp. Training camp was offered to me by my employer, so I didn't inquire about their references. (or did you mean what materials did they reference?) The material we used was the official ISC2 publication "Certified Cloud Security Professional Official (ISC)2 Student Guide." IMHO, this guide is very poorly written. But that's the subject for another thread.
17. Cloud computing is based on which approach to service delivery:
a) virtualization
b) thin client technology
c) Virtualization or thin client technology
d) Tightly coupled architectural models
I answered "a," but the correct answer was "c." Really?Just the fact that they have "or" in the answer made it not seem correct. That combined with not having heard about thin clients since the early days of the internet made that answer seem wrong.
So my take on this one: Not sure who wrote this question but I agree it is poorly written and in some ways what I would call a trick question. I am not a CCSP but I do not think you should find any questions on the exam like this one.
@altoflyer wrote:
65. A risk assessment is based on the following, in order:
a) vulnerability, threat, probability, impact, existing controls, and risk determination.
b) vulnerability, threat, impact, probability, and risk de3termination
c) threat, vulnerability, existing controls, probability, impact and risk determination
d) threat, vulnerability, probability, impact, and risk determination
I answer b, which matches my instructor's drawing in class. The correct answer is D.
My class notes and the photo of the instructor's drawing clearly says:
Identify assets
Identify vulnerabilities
Identify threats
Identify exposure factor (impact)
Identify Likelihood (probability)
Perform qualitative risk analysis
perform quantitative risk analysis. which means that my selected answer was correct.
HOWEVER ... between when I wrote that and now, I found this in the Student Guide:
Risk Management Process
An organization will conduct a risk assessment (the term risk analysis is sometimes intercahgned with risk assessment) to evaluate:
- threats to its assets
- vulnerabilities present in the envrionmnet
- the likelihood that a threat will be realized ...
- the impact that the exposure being realized will have on the organization
- Countermeasures available ...
- the residual risk
So that matches the right answer, D. So I guess that one is now answered. Go with the official ISC2 guidebook.
So I would have gone with D. Rationale: Patch Tuesday example: a threat is announced, you check to see if you are vulnerable (does it exist in your environment), then evaluate the likely hood (impact), and then determine what to do. The problem is that several of these steps happen at the same time. I am not a fan of questions that are lists that require memory work......
@altoflyer wrote:
135: Generally, there are two types of cooling, and the return air temperature is based on:
a) latent cooling (remove moisture) and sensible cooling (remove heat), and the temperature is measured at the inlet point.
b) latent cooling (remove moisture) and sensible cooling (remove heat), and the temperature is measured at the server exhaust point
c) latent cooling (remove heat), and sensible cooling (remove moisture), and the temperature is measured at the inlet point.
d) latent cooling (remove heat) and sensible cooling (remove moisture), and the temperature is measured at the server exhaust point.
Well that's just wrong. The air temperature is measured as it exits the room, not as it enters the room. My selected answer was: Latent cooling (remove moisture) and sensible cooling (remove heat),and the temperature is measured at the exhaust point.
Thoughts?
I know nothing about heating but as a casual user, I would rule out A and C and look to B or D as being the answer. I would probably go with B.
Others?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
For 17, if you consider IaaS, PaaS and SaaS than c) is probably more correct answer. Virtualisation is an enabler for cloud services, but thin client i.e. standard web browser, provides the universal access that make it usable. If you look at the NIST definition in SP800-145 that should explain.
32 seems to be a poorly worded question and set of answers.
For 65 if you look up 27005 or look at the links below, by convention you start with the threat source, then the threat actor who targets a vulnerability in an asset .....
https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-30r1.pdf
https://en.wikipedia.org/wiki/IT_risk_management#/media/File:2010-T10-ArchitectureDiagram.png
You've got all the right elements.
Steve Wilme CISSP-ISSAP, ISSMP MCIIS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> I got the practice test from Training Camp.
I taught for Training Camp several times, and I often had trouble justifying the
"correct" answers on *their* practice exams from *their* material ... (Training
Camp *used* to have some agreement to use ISC2 facilitators and material, along
with their own stuff, but I don't know what the current situation is ...)
====================== (quote inserted randomly by Pegasus Mailer)
rslade@vcn.bc.ca slade@victoria.tc.ca rslade@computercrime.org
The sun, with all those planets revolving around it and
dependent upon it, can still ripen a bunch of grapes as if it had
nothing else in the universe to do. - Galileo Galilei
victoria.tc.ca/techrev/rms.htm http://twitter.com/rslade
http://blogs.securiteam.com/index.php/archives/author/p1/
https://is.gd/RotlWB
............
Other posts: https://community.isc2.org/t5/forums/recentpostspage/user-id/1324864413
This message may or may not be governed by the terms of
http://www.noticebored.com/html/cisspforumfaq.html#Friday or
https://blogs.securiteam.com/index.php/archives/1468
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think it helps to stick to the official CBK materials rather than use secondary sources. The applies to the CISSP and CISSP concentrations (follow the references at the end of the chapters). Depending on reworked secondary sources, both in academia and in professional life is unlikely to be a useful shortcut. So if you need to read the SP800 series, IETF RFCs, CoBIT ISO 27000 series or whatever, go read the original.
Steve Wilme CISSP-ISSAP, ISSMP MCIIS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content