A new vulnerability in Dynamic Data Exchange protocol (DDE) in Microsoft Office has been discovered. The DDE protocol is a set of messages and guidelines, it sends messages between applications that share data and uses shared memory to exchange data between applications.
Attackers could exploit DDE to launch malware via infected Office file attachments, for example in Word and Excel files, by performing code execution without using macros, the applications that support DDE display no security warnings to victims, except asking them if they want to update the document with the data from the linked files. Then, victims would be prompted with a message informing them that the document contains links to external files, asking them to allow or deny the content to be retrieved and displayed:
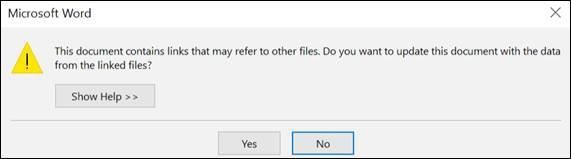
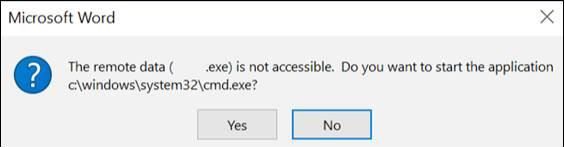
If allowed, the malicious document will communicate to the attacker hosted content in order to retrieve code that'll be executed to initiate the malware infection.
In addition, Outlook's emails that support Rich Text Format (RTF) can be exploited to launch DDE attacks without sending malicious Office attachments within email body.
How to Protect Yourself:
- Deny the content to be retrieved and displayed through the pop message by clicking "No".
- View all email messages in plain text format, if necessary.
- Ensure to open attachments from verified sources.
- Word Files: Disable the option below which listed under the general group on Options.
For More Information about DDE:
https://msdn.microsoft.com/en-us/library/windows/desktop/ms648774(v=vs.85).aspx