- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- Re: SHA 2 Vulnerability
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SHA 2 Vulnerability
Good morning,
As SHA-2 shares the same algorithm as SHA-1, aren't the hash lengths subject to the same type of attacks?
One would think that the industry would want to move to SHA-3 and avoid a repeat of the SHA-1 fiasco.
Am I wrong? Am I reading too much into it?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Since I am not a crypto-geek, I leave it to others to interpret. However, the search results from the CVE database and the National Vulnerabilities Database may help inform the discussion:
https://cve.mitre.org/cgi-bin/cvekey.cgi?keyword=%22SHA-2%22
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
SHA2 is designed to provide protection against hash collission attacks but does not improve resistance against brute force or dictionary-based attacks so the answer will depend on what you are using SHA* for and what your overall threat model looks like. If hash collissions are relevant to your threat model, migrating from SHA1 to SHA2 might be sufficient. If other attack types are more relevant, maybe you want to move to something else. In the end our job is to make it too expensive for an attacker to target our systems. If using SHA2 satisfies that need at an acceptable cost, it is good enough.
Note that the hash lengths of SHA1 and SHA2 are not the same. Where SHA1 has a 160b hash length, SHA256 and SHA512 provide longer hash lengths (yes, 256b and 512b respectively).
Sic semper tyrannis.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@clyoneer wrote:Good morning,
As SHA-2 shares the same algorithm as SHA-1, aren't the hash lengths subject to the same type of attacks?
One would think that the industry would want to move to SHA-3 and avoid a repeat of the SHA-1 fiasco.
Am I wrong? Am I reading too much into it?
Thank you.
Dude, there are fundamental differences in the construction of the hash functions. Check out this table:
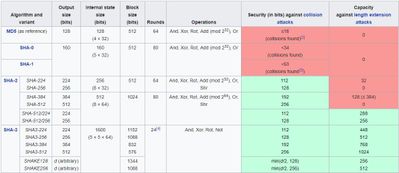
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you for your answer, which segways to the follow up question:
Isn't true that SHA-1 and SHA-2 share the same base Algorithm (SHA) and ultimate, some hash lengths are subject to the same type of attacks?
Public attacks on SHA-2 have been happening since 2008. Just like what happened with SHA-1, the attacks against SHA-2 have been getting increasingly better and weakening SHA-2 over time. Some attacks have SHA-2’s effective protection down to 237. Some of the latest attacks, publicly announced in 2016, consider SHA-2 attacks to already be “practical”.
I just want to make sure that the enterprise assets are appropriately protected and begin to plan the migration to SH-3 if is required.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@clyoneer wrote:
Thank you for your answer, which segways to the follow up question:
Isn't true that SHA-1 and SHA-2 share the same base Algorithm (SHA) and ultimate, some hash lengths are subject to the same type of attacks?
Public attacks on SHA-2 have been happening since 2008. Just like what happened with SHA-1, the attacks against SHA-2 have been getting increasingly better and weakening SHA-2 over time. Some attacks have SHA-2’s effective protection down to 237. Some of the latest attacks, publicly announced in 2016, consider SHA-2 attacks to already be “practical”.
I just want to make sure that the enterprise assets are appropriately protected and begin to plan the migration to SH-3 if is required.
You can use this tool to make a risk informed decision : https://www.keylength.com/en/2/
tl;dr -- it would be estimated that a hash length of 170 bits should be sufficient to last you into 2025.
Note : it would be kind to either tag the person that you're replying to and/or quote their original reply so it is easy for people to continue a conversation. Specifically your "This is not what I was asking" reply comes across badly because nobody knows who you are replying to. I don't see any responses that are not relevant to your original question.
Sic semper tyrannis.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@wimremes wrote:
You can use this tool to make a risk informed decision : https://www.keylength.com/en/2/
tl;dr -- it would be estimated that a hash length of 170 bits should be sufficient to last you into 2025.
Note : it would be kind to either tag the person that you're replying to and/or quote their original reply so it is easy for people to continue a conversation. Specifically your "This is not what I was asking" reply comes across badly because nobody knows who you are replying to. I don't see any responses that are not relevant to your original question.
@clyoneer Thank you. You are correct. I will remove that particular reply shortly.
