- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- Injection Flaws- Long Trending Security Risk
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Injection Flaws- Long Trending Security Risk
Good day All,
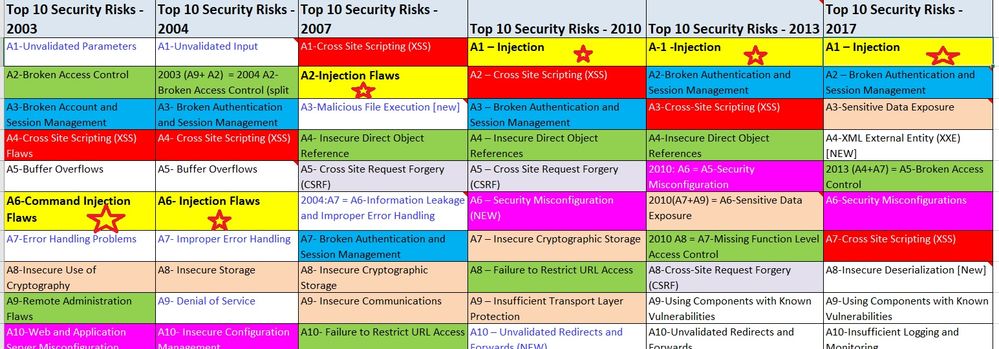
Injection flaws are trending in OWASP top 10 security risks for the last 15 years. It's No.1 risk.
Interestingly moving from A6 to A2 to A1 (Please see the pic)
There are many sophisticated injection vulnerability scanning tools, code analysis tools , pen test tools available, there is a lot of awareness about this risk.
Injection flaws are easy to discover when examining code, but frequently hard to discover via testing. Scanners and fuzzers can help attackers find injection flaws
despite of it... it's raising... can't we defend against it to bring it down 99% ? I know that there is no guarantee for 100% security in the world, if someone says it's a myth, however my question is why it's standing at the top of the list?
I'm curious to see a best solution and root cause of it.
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great questions.
I'm going to limit my response to SQL injection vulnerabilities.
No matter how often I urge people to avoid dynamic SQL, they continue to use it. Obviously, dynamic SQL can be made safe through through data escaping and other related hygiene.
I've been working with SQL since the very earliest days of DB2, and back then we were forced to deploy parameterized procs that were written by our DBA team because DB2 was so inefficient back then. Ironically, that may still be the best approach - not for performance, but to help safeguard against SQL injection attacks.
Generally speaking, I don't think we pay enough attention to demonstrating what the bad guys can do with injection attacks. We can use the famous Hack Me Bank.... But I've found big improvement when developers actually see what an injection attack can do.
Obviously, building dynamic and static scanning into the SDLC so that developers can test their own work products while they're in the development phase is quite effective. And at first, it's probably going to be necessary to ensure such scanning is taking place.
Of course, a comprehensive pen testing program is also required, but it really shines when the other steps are taken earlier in the SDLC.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
> iluom (Newcomer II) posted a new topic in Tech Talk on 01-09-2019 06:37 AM in
> I know
> that there is no guarantee for 100% security in the world, if someone says it's
> a myth, however my question is why it's standing at the top of the list? I'm
> curious to see a best solution and root cause of it.
Unfortunately, the root cause is stupidity (on the part of developers), and, equally unfortunately, there is no solution to stupidity. Constant vigilance is the price of having all kinds of creative people building interesting (and all-too-often-useless) stuff without having to go through formal processes of education and certification.
............
Other posts: https://community.isc2.org/t5/forums/recentpostspage/user-id/1324864413
This message may or may not be governed by the terms of
http://www.noticebored.com/html/cisspforumfaq.html#Friday or
https://blogs.securiteam.com/index.php/archives/1468
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
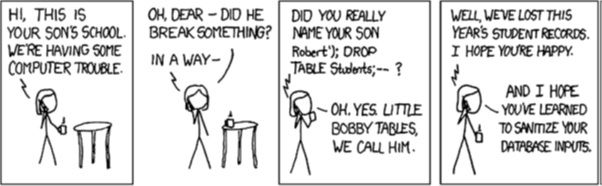
SQL Injection Illustration
Image Courtesy : xkcd.com