- ISC2 Community
- :
- Discussions
- :
- Tech Talk
- :
- Improving email communication behavior (or, "Be th...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Improving email communication behavior (or, "Be the change you want to see")
Your users endure year after year of Security Awareness Training which repeatedly say, "Don't click on links / attachments", or "[insert your org's preferred response to UCE here], then delete". And year after year, campaign after campaign, people still click on links and open attachments.
A question I recently read on LI said it's hard to counter this behavior because HR (or legal, or finance, or whomever!) constantly send messages which subvert the SAT. Which is to say, that users should not really be held at fault when using such mediums exactly as they're intended to work.
It's unfortunate for users who are repeatedly told to NOT CLICK, and then receive official communication which FORCE CLICKING. So I'd like to hear ideas on changing behaviors so that both SENDERS and RECIPIENTS adhere to something safer.
What does your enterprise do (in terms of policy, controls, communication) to shift behaviors?
A claim is as good as its veracity.
linkedin[.]com/in/geater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
This is the LI post, for those who'd like to read and respond:
A claim is as good as its veracity.
linkedin[.]com/in/geater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Honestly, I can't complain about our SATE program because it has lowered the click rate to almost zero on our monthly phishing campaigns. We have a mandatory annual video training and weekly security reminders emailed out to keep it top of mind. Telling them not to click doesn't work but telling them to stop, think, then click is an effective strategy for success here. Can't wait to hear what others have to say!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@gidyn I mean...it has a power button as well. We could always go that route and see what happens. 😉
In all seriousness though, I've seen some replace the actual link with a safe link. I believe it was an O365 security setting that did it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@tmekelburg1 when you say "safe link" do you mean that every link is automatically sandboxed and tested, or all links are forcibly made neutral, and may only be sent through explicit permissions?
A claim is as good as its veracity.
linkedin[.]com/in/geater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
https://www.proofpoint.com/us/products/email-security-and-protection/email-protection has functionality to screen all links in emails.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
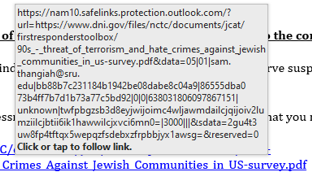
I can't say exactly since it's not my system on what it does but here's an example screenshot. It keeps the original text of the link but when you hover over it, it shows this:
It redirects to the original link after clicking on it.
Edit: Looks like Defender for O365 after looking into it more. Proofpoint probably does something very similar as @gidyn suggested.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
@ericgeater wrote:
..."safe link" do you mean that every link is automatically sandboxed and tested, ....
Kinda this. We have one of these at my employer. Links in our emails are replaced with unique links to the safe link web site. When somebody clicks on a link, the safe link site scans the real page and "proxies" its content to the user, much like any web-browser url filtering product would do.
The purported good:
- Links get "security scanned" regardless of web-browser config.
- Scanning is delayed until use, so one benefits from knowledge gained between the time of mail-sending and mail-reading (e.g. if it was blasted to many safe link customers).
The bad:
- It is more difficult for users to visually inspect URLs
- More complexity, more money, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Looks like @gidyn and @tmekelburg1 have shown some useful controls. Excellent, and thank you. Those are useful because they can thwart the behavior of an unwitting user. And I saw that training is definitely key. Totally agree there.
A claim is as good as its veracity.
linkedin[.]com/in/geater