- ISC2 Community
- :
- Discussions
- :
- GRC
- :
- Strategic Value Risk Equation (SVRE) - Risk manage...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Strategic Value Risk Equation (SVRE) - Risk management
Hi All
One of my colleagues from the ISC2 Auckland Chapter developed this methodology called Strategic Value Risk Equation (SVRE), do you think it has merit, legs even and could be used actively within organisations even your own? Or is it similar to other methods and approaches?
The youtube link of the ISC2 Auckland Chapter session is here:
https://www.youtube.com/watch?v=RoPSGjr0Ajw
Assess for yourselves, Gabriel the author would appreciate this.
Regards
Caute_Cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Maybe. On his next presentation, I'd ask him to take us through a scenario and plug in the values as we go through the equation.
For example, setup any pre-determined values and walk us through the equation below:
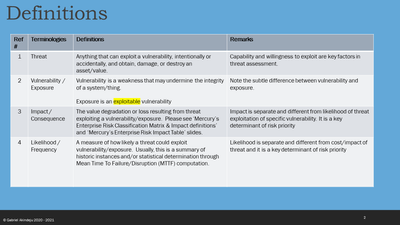
To determine our risk profile on a specific threat:
- Threat intel feeds notify us of a threat (Insert value)
- Our exiting technical controls help mitigate or lower risk (Subtract from Insert Value)
- Vulnerability scan tells us we are vulnerable to the threat and by how much (Add to Insert Value)
- Our general controls also help mitigate and lower overall risk to the Org (Subtract from Insert Value)
I'm not entirely sure what to do with the equation after that. I'm sure it's in the presentation somewhere but it's over my head.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please see pdf version of this response at: https://drive.google.com/file/d/1icTVgIUIbH3dLZhnT-ieP-rnvaMf6Opi/view?usp=sharing
Step Through
- Let us initially assume a green-field environment. No existing exposures [we will come to dealing with existing exposures of brown-field environment later].;
- So, say the Board of Directors, through its delegations, determine a certain Risk Appetite level Rp;
- Through empirical data for this green-field environment, we determine that to meet and operated within acceptable tolerances around Rp, the maximum Vulnerability Threshold, VT ,that could be allowed into the environment [for instance using the CVSS] is CVSS=3. Please note that the SVRE for (eqn-2) can be used to solve for VT;
- Assuming, the General Controls, CG, environment of this green-field environment assessed at CMM-3 and is designed and operated sufficiently enough to withstand current Threat Threshold TT [MITRE 2 – Limited];
- Putting all of those into the eqn-1 could be made a scalar equation as below:
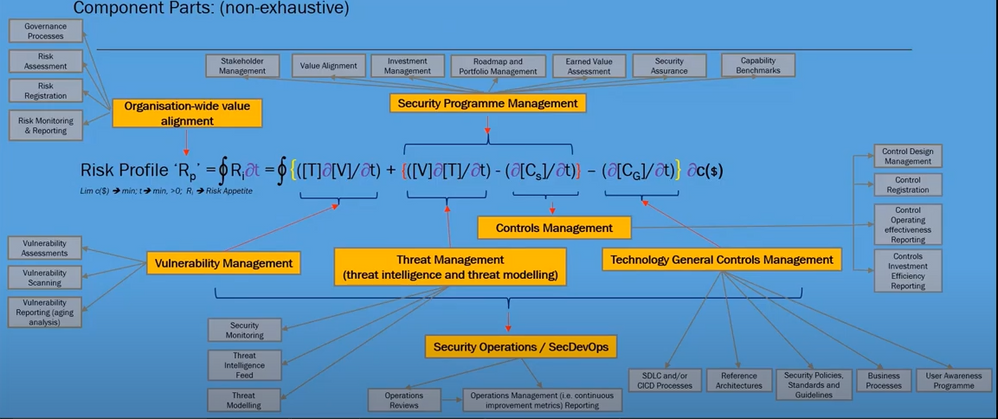
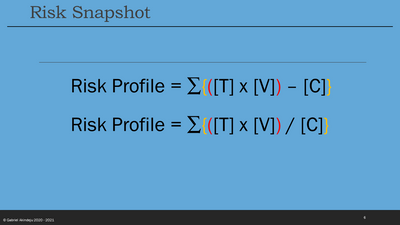
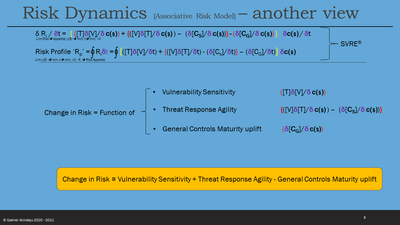
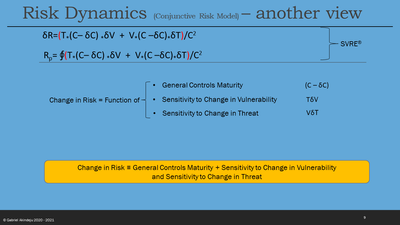
- Ri2 - Ri1 = {(T x (V2 – V1) / ($NZ2 - $NZ1)) + { (3 x (T2 – T1)/ ($NZ2 - $NZ1)) - (CS2 – CS1)/ ($NZ2 - $NZ1)} – (CG2 – CG1)/ ($NZ2 - $NZ1)} ($NZ2 - $NZ1)/ (t2 – t1)
- If we assume 1 reporting period, for simplicity, t2 – t1=1 and NZ$1 new investment then:
Ri2 - Ri1 = {(T x (V2 – V1)) + {(3 x (TT2 – TT1)) - (CS2 – CS1)} – (CG2 – CG1)}
- Inserting figures from statements #3 & #4 above:
Ri2 - Ri1 = {(T x (V2 – 3)) + {(3 x (TT2 – 2)) - (CS2 – CS1)} – (CG2 – 3)}
c-1: ($NZ2 - $NZ1) = Value of investment in specific Risk Management domain, in this case Technology Risk Management and Mitigation Controls (Security);
c-2: (CS2 – CS1) = additional supplementary controls implemented leveraging additional investment ($NZ2 - $NZ1);
- From statement #5(c): it may be apparent that to keep Ri [Ri2 - Ri1 =0] at about within the set tolerance of Risk Appetite Rp, the following must occur in correlation with changes in introduced exposed vulnerabilities and/or change in threat landscape:
- An increase in introduced vulnerabilities [from V=3 to a new level V2], especially if exposed, will necessitate additional supplementary controls, (CS2 – CS1), which will require additional investments;
- An increase in impacting threat position [from T=2 to a new T2] will necessitate additional supplementary controls, (CS2 – CS1), which will require additional investments;
- It is possible to so adjust the operation of the SVRE to optimise investment and value derived by setting and enforcing threshold VT.
- Step-Through statements #3-6 above are simplified view of risk dynamics. In reality, the risk and threat landscapes could be extremely active, and with different components moving and evolving at different paces and phases. For these reasons, a simplistic view as in above, is at best an approximation -good agile and adaptive risk leadership.
- Each of Threat, T; Vulnerability, V; Controls, C; are vector variables and the interactions between these vector variables are modelled as cross-multiplication to enable rich path-dependent analysis;
- The SVRE, in its full strength, could be solved through the application of Field Theory and/or Numerical Calculus.
I will be happy to respond to additional queries/requests. I am keen to see how you (and others) see the SVRE. If it could be helpful or not. What must be tweaked to make it more applicable and helpful to everyday risk management processes?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gabriel
Can I make a suggestion, is it possible to create Macro's which create a form for the entry of values, which output in the form of graphics or graphs, this may provide deeper insight for potential users in terms of pictorially see the effects of the changing values they input?
Then the idea, and getting across that idea, may be more meaningful? As I suggested purely a suggestion to make the idea come alive? This would be an idea problem for a Quantum Computer, taking the various inputs from the organisation and then computing the effects of those changes across set parameters or limits as you suggest.
It may provide a more meaningful way of some people seeing the effect of their decisions rather than having to be mathematical geniuses? This way it would be more meaningfuly to them? Is this possible to do from Excel Macro's within Microsoft Word or similar means?
I know it means locking into certain scenarios, but this may be more insightful to people who do not have your insight via mathematics and prefer to see the results and changes via graphical means?
For instance when designing aerials, for certain frequencies, I tend to use tools, which do the mathematics, but one can see the effect of the changes being input across different scenarios for example.
Regards
Caute_cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thanks JM,
Actually, I have a complimentary risk assessment workbook/tool that I can share. We use it internally for a number of discussions and assessment work. I will unlock the Risk Appetite definition section, so that the wider community may be leverage and define their own appetite statements.
The tool immediately tells you if a mitigation step is worth the effort and cost; and also provides efficiency metrics. In the future, this will be developed and deployed on a proper computing platform.
How does one share files on here without linking via google-drive?
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Gabriel,
When you create a message you can create up to two attachments up to the size of 9.8 Mbytes in size.
You can drag and drop or upload the files without using Google Drive.
I suggest it should be from your computer, without any inter linkages.
The other way is for me create a link via IBM Box, and then people can request access to it individually - I can then allow or deny them access accordingly.
Regards
Caute_cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We had a very productive and engaging seminar at the NZISF, in Auckland, on 8th July, 2021. A view of some post seminar interactions on the attached.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi JM,
I shared workbook with you. Kindly create secure access and release protocol.
Regards
Gabriel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi colleagues,
If you would like access to a companion workbook with some applications of the SVRE concepts (not all, at this stage), please see:
https://ibm.box.com/s/b1v79k5xqpx9c4h75pfq4cm099ufam2z
You may need to request access.
Thanks to JM for his assistance with this.
Sincere regards
Gabriel
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi colleagues,
If you would like access to a companion workbook with some applications of the SVRE concepts (not all, at this stage), please see:
https://ibm.box.com/s/b1v79k5xqpx9c4h75pfq4cm099ufam2z
You may need to request access.
Thanks to JM for his assistance with this.
Sincere regards
Gabriel