- ISC2 Community
- :
- Discussions
- :
- Cloud Security
- :
- Re: Asymmetric Encryption - Quality of Material? C...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
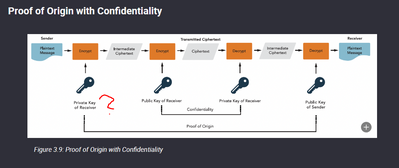
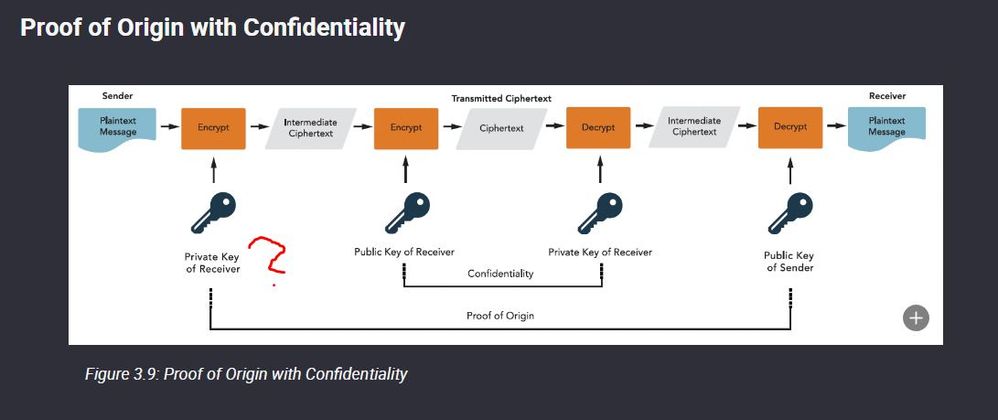
Asymmetric Encryption - Quality of Material? CCSP Course 5th Edition.
Either this picture has an massive error or I am to stupid 😄
Can someone confirm one or the other?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
So Encryption is not my strong suit but I would say the Diagram is WRONG.
From my trainings, I have always been told not to share my PRIVATE key with anyone.
I believe this should be escalate to the training material development team for verification. @Kaity would be kind enough to pass along.and quite possibility see if there is an errata for this.
My take would be:
Proof of Origin:
Message - signed by sender's private key - using the sender's public key to validate the sender.
Confidentiality:
Message - encrypted using the receiver's public key and decrypted using the receiver's private key.
Others?
d
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Yes, an error. As you note, the first action is done with "private key of sender". The general idea of public-key encryption is that everyone keeps their private key confidential and gives their public key to everyone. So, only the sender can use the sender's private key and only the receiver can use the receiver's private key.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Many thanks, for a moment I thought I am really going nuts 😄
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Upon reflection, it is also important to know that it is called a public-private keypair because the two work in tandem, with the public key undoing whatever the private key did. Similarly, the private key undoes whatever the public key does.
The keys cannot "undo" their own actions. Using the same key twice (as the diagram shows) would put you further away from the original cleartext. This one little detail is what makes Public-key (asymmetric) encryption substantially different than shared-secret (symmetric) encryption.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi all
Well as the federal government state get prepare for your post quantum encryption, because Public Key encryption will be dead as a door nail, as other nations are collecting as much encryption traffic as they can, so they can decrypt it when they have sufficient quantum encryption and related computing available to them.
Quantum computers pose a serious threat to today's digital security due to their ability to factor numbers into primes much faster than their classical counterparts. Shor's and Grover's algorithms provide the mathematical foundations for quantum computers' threat to current encryption.
Regards
Caute_Cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Was this found here at (ISC)2's online learning portal? Or was this on another site? That wasn't made clear.
A claim is as good as its veracity.
linkedin[.]com/in/geater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Eric- General reading and collection of information, but if you want references:
https://post-quantum.com/the-quantum-threat/index.html
Regards
Caute_Cautim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, Caute, I'm very grateful for your thorough response! But I was responding to the original poster, as I did not know the source of their image snip. I've now surmised that it's from an online student guide, assuming it's apparently managed by (ISC)2 or a publishing partner.
Which is to say, @AndreaMoore it's difficult to follow replies on this forum. A thread becomes somewhat difficult to follow, if I can't determine if a new response follows the post or a subsequent reply. Am I missing something?
A claim is as good as its veracity.
linkedin[.]com/in/geater
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you want to reply to someone specific use the @ symbol and you can also reply to a specific message/post and also to make it clear you are commenting on a specific part of the message use the "quote" button. I've just used the " button and since I'm replying to your post it quoted yours. I also edited which part I quoted of yours so you know I'm only responding to the part I'm referring to.
I hope this helps. But yes, it can be confusing when people just reply and responses overlap - using the @ symbol and the " button would help.
@ericgeater wrote:
Which is to say, @AndreaMoore it's difficult to follow replies on this forum. A thread becomes somewhat difficult to follow, if I can't determine if a new response follows the post or a subsequent reply. Am I missing something?
ISC2 Community Manager