- ISC2 Community
- :
- CISSP Study Group
- :
- Forum
- :
- Why not authenticate the whole packet in ESP mode?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Why not authenticate the whole packet in ESP mode?
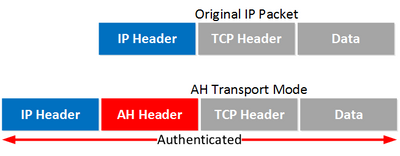
In AH:
- a) Transport Mode:
Entire packet Authenticated
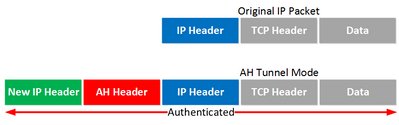
- b) Tunnel Mode:
Entire packet authenticated
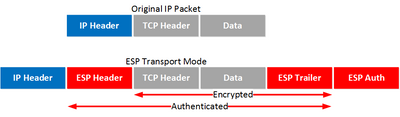
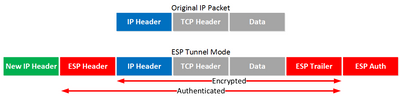
In ESP:
1) Transport Mode:
Only ESPH-ESPT authenticated
Original IP Header not authenticated.
2) Tunnel Mode:
Only ESPH-ESPT authenticated
New IP Header not authenticated.
Why is this difference found in them? Is there a reason behind them? Why not authenticate all of the packet? What problem would it create?
And why is there no such thing called AH auth but there's ESP Auth? Shouldn't AH Auth data also be in the figure shown above?
Also, Is there a reason why the modes are named "Tunnel" And "Transport"?
Source:https://networklessons.com/cisco/ccie-routing-switching/ipsec-internet-protocol-security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think the short answer to your question is there are times when you don't want to authenticate the header (e.g., NAT). Then there are times where you want to authenticate the IP header (to ensure no tampering with source of destination).
ESP can authenticate the data, not the actual header. If your concern is just the integrity of the data, then ESP and AH are equivalent in that regard, but if you want to ensure both the header and data have not been tampered with, AH is the option. Flip side is AH won't work across because NAT needs to change the IP header.
I'm not sure about your question regarding why there is nothing known as "AH auth." It would be a little redundant, I suppose. Authentication Header (AH) protocol is only about authentication (inserts a hash to confirm integrity). Encapsulated Security Protocol (ESP) can be used for either authentication, confidentiality, or both. Their function is a bit different. Or think of it this way, ESP can take an entire packet (including an AH one), encapsulate it, apply encryption to achieve confidentiality, while also adding its own payload hash to ensure integrity. It's not one or the other. AH can even be used with ESP.